In a previous blog post, I talked about the three key aspects of managing your databases – security, performance and availability. I call it “taking your databases to a S.P.A.” In the blog post, I referred to an infographic that Idera published about their accidental DBA survey results, highlighting how security and availability are not getting as much attention as dealing with performance issues.
Now, I’m a bit paranoid with security. Having come from “the dark side” before cyber crime laws were even introduced, information security is something that I have been very concerned about because of its impacts not only on computer systems but also on the lives of people that are affected by it. Take a look at this visualization of the world’s biggest data breaches. Shocking and scary, isn’t it?
While the main theme of my blog posts are mainly on high availability and disaster recovery (HA/DR,) it’s important to highlight that security plays a very important role to keep systems available. A couple of years ago, one of my customers asked me to investigate why one of their public-facing websites take a while to respond to user requests. After finding out that the culprit was the database, I started digging deeper. It turns out that the website is experiencing massive blocking on a specific table because it was exploited by a SQL injection attack. And because of this, users can barely access the system.
When Security Translates to Availability
I always start every high availability and disaster recovery project with the definition of the recovery objective (RPO/RTO) and service level agreements (SLAs.) I also emphasize that SLA is not just how quickly you can restore your database back online but how the end users can interact with it. It doesn’t matter if you managed to restore database operations within 5 minutes and have met your SLAs but if the end users cannot access the application or the performance is affecting response time, it is technically offline. It’s the end users’ perception of availability that defines whether or not something is available.
What’s even worse is that when a system is compromised, not only is the application at risk to the attacks but it also becomes unavailable as a side effect, hence, impacting availability. I’ve seen cases where a database system became unresponsive and eventually unavailable as a result of a denial of service (DOS) attack.
Being Proactive With Security
Whether or not you are managing databases or systems with sensitive data, you need to be proactive with monitoring, analyzing and implementing security best practices. Jay Paloma, a Windows Experience (previously Security) MVP (blog | Twitter) taught me this very important lesson years ago:
Security is a state of mind. Share on X
Think about some of the things that you do at home to keep yourself, your family and your assets safe.
- – You don’t leave your doors open even when you’re at home
- – You don’t tell or give everyone your garage door key codes or keys
- – You don’t let your friends come near your safety box when they visit
I can go on and on about the different things that you do at home to maintain security. In the same way, securing computer systems require constantly thinking about protecting them and implementing security best practices. If you don’t know where and how to start, refer to the graphic below on Defense in Depth.
Defense in Depth for Database Systems
Securing database systems can be overwhelming because of all the complexities required to keep them safe. To simplify the process of getting started, start with defense in depth – the process of implementing multiple layers of security to minimize vulnerability and protect a system. You can use this guide as a reference. Note that you and the rest of your IT team should be responsible for the different layers mentioned below. This isn’t a one-man sport.
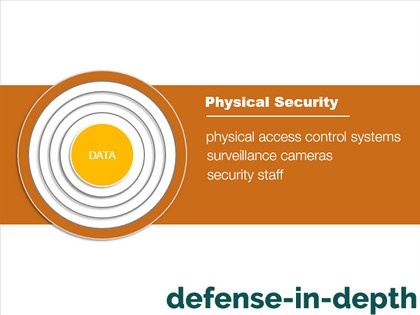
Your servers should be physically protected
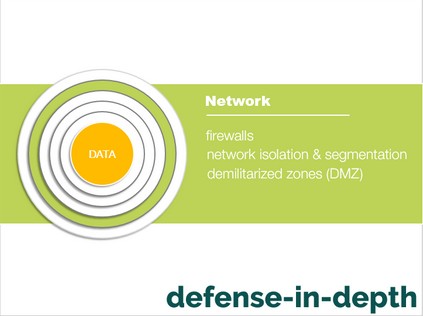
Your network administrators should be responsible for this
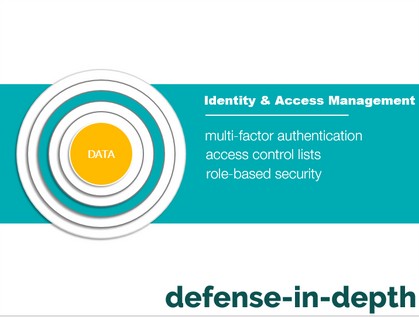
You and your systems administrator should be responsible for this
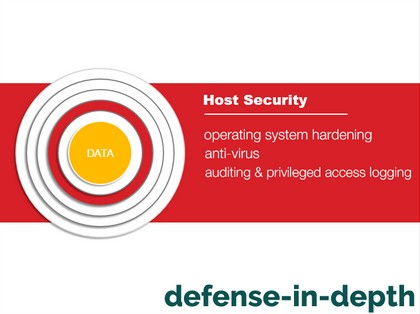
You and your server administrator should be responsible for this
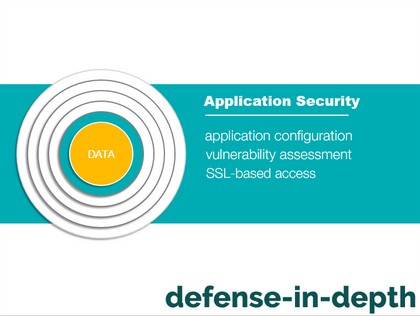
You and your applications team should be responsible for this
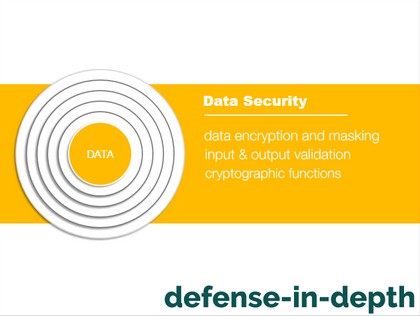
You are primarily responsible for this as a DBA
Call To Action
Take a look at some of your security strategies and understand how they could affect your database availability. Use the principle of defense in depth mentioned above to start evaluating database systems and your entire IT infrastructure. Get everyone on your team on board on how to secure and protect your IT assets. Remember, a security vulnerability can greatly impact your system availability